Table of Contents
Introduction
Protecting business data is a non-negotiable priority. A single breach can damage customer trust, regulatory standing, and financial stability. Microsoft Dynamics 365 security model ensures that organizations maintain strict control over their data with role-based access controls, encryption, auditing, and compliance management.
More than just restricting access, security in Dynamics 365 is designed to enable secure business processes, streamline compliance, and enforce data privacy at every level. By implementing a structured security framework, businesses can reduce risk, meet regulatory requirements, and safeguard sensitive information without disrupting operations.
This blog breaks down how the Dynamics 365 security model works, its key components, and best practices for implementation—ensuring your system is both protected and optimized for efficiency.
Overview of Dynamics 365 Security Principles
Microsoft Dynamics 365 embraces a vigorous security model designed to safeguard sensitive information, control user access, and ensure compliance with global regulations. This security model is built upon four key principles: security, privacy, compliance, and transparency.
Security: Protecting Against Cyber Threats
Privacy: Ensuring Data Ownership and Control
Compliance: Adhering to Global Standards and Regulations
With increasing regulatory requirements across industries, Dynamics 365 is designed to help businesses stay compliant with a variety of global standards and laws. The platform integrates with several compliance tools and frameworks to help businesses meet data protection requirements, including GDPR, HIPAA, and more. By following these compliance guidelines, businesses can mitigate risks related to data security and privacy violations.
Transparency: Maintaining Clear Communication about Data Handling Practices
Transparency ensures that businesses are fully aware of how their data is being handled, stored, and processed. Dynamics 365 provides clear insights into data access and usage, offering detailed logs and reporting to help organizations track who has accessed what information and why. This openness builds trust with customers, stakeholders, and regulatory bodies by demonstrating commitment to ethical data practices.
Core Components of the Dynamics 365 Security Model
Dynamics 365 employs several core components to build a comprehensive security model that addresses businesses’ unique needs. These components help define data structure and accessibility, ensuring that only authorized users have the right level of access.
1. Business Units: Structuring the Organization to Manage Data Access
Business units within Dynamics 365 are used to create organizational hierarchies, which help control how data is accessed and shared. Each unit can have its own security policies, which allows organizations to tailor access controls based on the department, geographic location, or role of employees. This structure enables businesses to segregate data and limit exposure to sensitive information based on user needs.
2. Security Roles: Defining Permissions and Access Levels for Users
Security roles play a critical role in the Dynamics 365 security model by determining the permissions users have within the system. Each role is assigned specific permissions that define what actions a user can perform, such as creating, editing, or deleting records. By assigning users to appropriate roles, organizations can ensure that each employee has access to only the data necessary for their job functions, reducing the risk of unauthorized access.
3. Users and Teams: Assigning Roles and Facilitating Collaboration While Maintaining Security
Ready to Strengthen your Data Security with Dynamics 365?
Ensure a secure, compliant, and optimized Dynamics 365 security model with AlphaBOLD. Our experts help you implement role-based security, record-level access, and field-level protection tailored to your needs.
Request a DemoLayers of Security in Dynamics 365 Security Model
Microsoft Dynamics 365 security model provides multi-layered protection, ensuring strict data access control at every level. With role-based, record-based, and field-level security, businesses can define permissions, restrict access, and safeguard sensitive information. This customizable framework enables organizations to enforce granular security measures without disrupting operations.
Role-Based Security: Controlling Access Based on User Roles Within the Organization
Role-based security is one of the cornerstones of the Dynamics 365 security model. It controls user access by assigning permissions based on the user’s role within the organization. This ensures that individuals can only access and perform tasks that are relevant to their job function. By clearly defining roles and permissions, businesses can limit data exposure to only the necessary stakeholders, reducing the risk of unauthorized access.
For example, an employee in the sales department might have access to customer contact information and sales opportunities, while a member of the HR department might only have access to employee records. Roles in Dynamics 365 can be tailored to match the business’s specific needs, ensuring that each user has appropriate access to data critical to their work but not beyond.
Roles can also be inherited from higher-level roles, which makes it easy to manage permissions for employees across different levels of the organization. By combining role-based security with other access controls, businesses can implement a least-privilege security model, ensuring that users only have access to the minimum necessary information to perform their tasks.
Record-Based Security: Managing Access to Specific Records Through Ownership and Sharing Settings
Record-based security adds another layer of protection by controlling who can access specific records within Dynamics 365. This level of security is important because it allows businesses to define who owns a particular record and who can share it. Ownership and sharing settings determine the visibility and accessibility of each record, ensuring that sensitive data is only shared with authorized users.
Ownership plays a key role in record-based security. The owner of a record has full control over that record and can assign access rights to other users. This allows organizations to set clear boundaries for data access. For example, a project manager who owns a project record can grant access to the team working on that project but prevent others outside of the team from viewing or editing the record.
Sharing settings provide even more flexibility, allowing users to share records with others while maintaining control over what those users can do with the record. Dynamics 365 allows for selective sharing, where users can provide read, write, or delete access based on their specific needs. This fine-tuned control helps businesses balance the need for collaboration with data security, ensuring that only the right people have access to the right records.
Field-Level Security: Restricting Access to Sensitive Data Fields Within Records
Field-level security takes security a step further by allowing businesses to control access to specific fields within a record. This is particularly useful for sensitive or confidential data, such as financial information, personal details, or proprietary business data. With field-level security, administrators can define which fields can be viewed or edited by specific users, providing an additional layer of protection.
For example, in a customer record, a user might have access to general contact information, such as the customer’s name, phone number, and email address, but not have access to financial details like credit score or payment history. Field-level security enables this level of granularity, so only authorized users, such as managers or finance team members, can access or modify sensitive data fields.
Field-level security is typically configured at the field level within the system, allowing administrators to set permissions for individual data fields. This provides a highly granular approach to security, ensuring that even within a record, only the necessary information is accessible to each user. Field-level security is especially important for industries dealing with sensitive personal data, such as healthcare and finance, where strict compliance with regulations like GDPR and HIPAA is required.
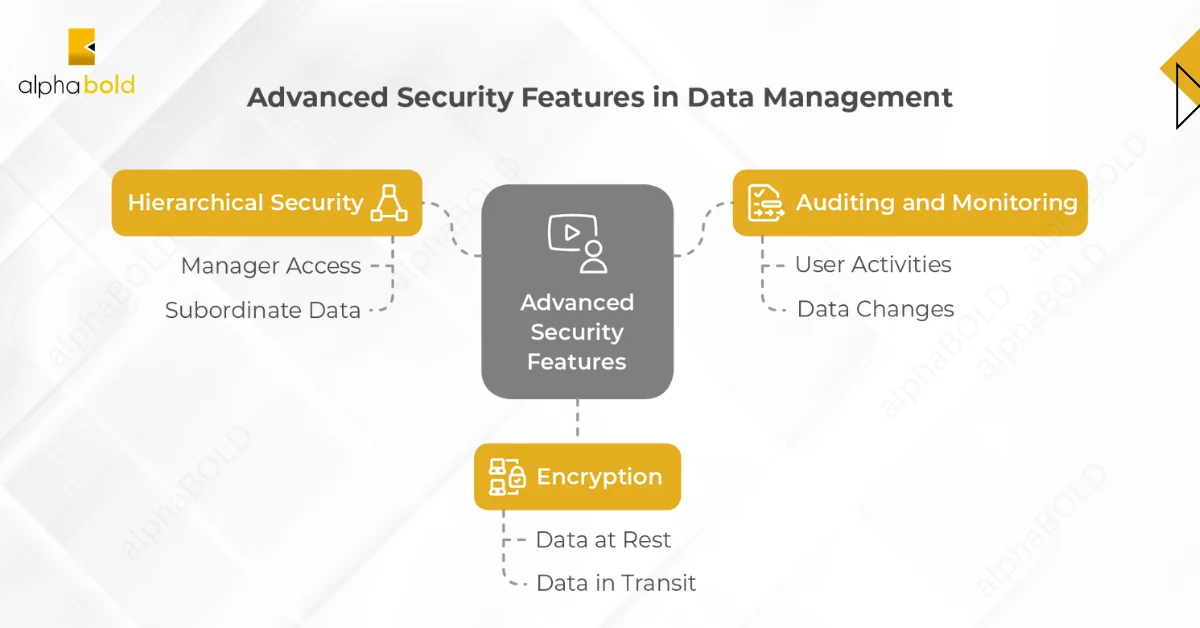
Advanced Security Features
- Hierarchical Security: Allowing managers to access the data of their subordinates based on organizational hierarchy.
- Auditing and Monitoring: Tracking user activities and changes to data for compliance and security purposes.
- Encryption: Protecting data at rest and in transit using industry-standard encryption protocols.
Best Practices for Implementing Security in Dynamics 365
Explore the best practices to protect your Dynamics 365 Customer Engagement environment: Securing Your Dynamics 365 Environment with Best Practices.
Regular Security Audits: Conducting Periodic Reviews to Identify and Address Vulnerabilities
Regular security audits are one of the most effective ways to maintain a secure environment in Dynamics 365. Periodic reviews of security configurations help organizations identify potential vulnerabilities and areas for improvement before malicious actors can exploit them.
Security audits should focus on several critical areas, including user roles and permissions, record sharing and ownership settings, and field-level security configurations. Organizations can minimize the risk of unauthorized access by reviewing who has access to what data and ensuring that access levels are appropriate for their job functions.
Audits should also assess whether security best practices are being followed, such as adherence to the principle of least privilege, where users are only granted the minimum access required for their work. Additionally, it’s important to ensure that security policies are aligned with evolving business needs and regulatory requirements. Regular audits not only help you identify risks but also provide an opportunity to improve security processes and keep your system compliant with the latest standards.
User Training: Educating Employees on Security Protocols and the Importance of Data Protection
Human error is one of the leading causes of security breaches, which is why user training is a crucial aspect of your security strategy. While Dynamics 365 offers a powerful security framework, employees must be educated on using the system securely and following best practices to protect sensitive data.
Training should focus on key security topics, such as using strong passwords, recognizing phishing attempts, and following safe data-sharing practices. Employees should also be educated on their responsibilities regarding data privacy, especially in regulated industries like healthcare, finance, and retail. Understanding the impact of data breaches on both the business and its customers can motivate employees to take security protocols seriously.
Training should not be a one-time event but an ongoing process, with regular updates and refresher courses to ensure employees stay informed about the latest security risks and practices. Additionally, creating a workplace security awareness culture can help foster responsible data handling and prevent inadvertent violations.
Data Backup and Recovery: Implementing Robust Backup Solutions to Prevent Data Loss
Having a reliable data backup and recovery plan is critical for business continuity in the event of a system failure, cyberattack, or natural disaster. Dynamics 365 provides various data protection mechanisms, but businesses must ensure that they have implemented robust backup solutions tailored to their needs.
A strong backup strategy should include regular, automated backups of all important data, including user records, business transactions, and system configurations. Backups should be stored in multiple locations, such as cloud storage and on-premise servers, to reduce the risk of losing data due to hardware failures or other unforeseen events.
Testing your backup and recovery processes is just as important as having them in place. Periodically test your ability to restore data from backups to ensure that the process works smoothly and quickly when necessary. A tested and well-documented disaster recovery plan will help your organization recover quickly in case of an emergency, minimizing downtime and protecting your critical business data.
Staying Informed: Keeping Abreast of the Latest Security Updates and Patches from Microsoft
Microsoft provides regular security patches and system updates designed to address known vulnerabilities, fix bugs, and enhance functionality. By staying on top of these updates and testing them before deploying them to production, you can ensure that your system remains secure and current. Implementing a proactive update strategy involves monitoring Microsoft’s security advisories, subscribing to relevant notifications, and keeping an inventory of all patches and updates applied to your Dynamics 365 environment. This will help you maintain a secure system and avoid potential security threats.
Additionally, staying informed means understanding the broader security trends that might affect your business. Whether it’s new compliance regulations or emerging cyber threats, being aware of these trends enables you to adjust your security strategy to meet evolving challenges and ensure long-term data protection.
Explore the latest updates: Dynamics 365 Support: Navigating Microsoft’s Updates .
Secure and Optimize your Dynamics 365 Environment
Ensure a secure, efficient, and compliant Dynamics 365 implementation with AlphaBOLD. Our experts help you navigate key security features and best practices to protect your business from potential threats.
Request a DemoConclusion
A strong Dynamics 365 security model is essential for protecting business data and ensuring compliance. Organizations can control access, reduce risk, and maintain operational efficiency by implementing role-based, record-based, and field-level security. AlphaBOLD helps businesses navigate Dynamics 365 security, ensuring a secure, compliant, and optimized setup. As a certified Microsoft partner, we provide tailored consulting, implementation, and support to safeguard your data.
For more information on how AlphaBOLD can assist you in optimizing your Dynamics 365 experience, visit our website.
Explore Recent Blog Posts